Based on a report, Borat named a brand new distant entry trojan (RAT) that appeared on darknet markets, which affords easy-to-use options to conduct UAC bypass, DDoS assaults, and ransomware deployment.
Cyberattacks have elevated rather a lot these days, even on excessive status tech firms. Lately a hacking group named Lapsus$ has breached data from companies like Samsung, Nvidia, Ubisoft, and Microsoft.
The RAT’s builders determined to call it after the principle character of the comedy film collection Borat, which featured the favored Sacha Baron Cohen because the protagonist. Nonetheless, this malware is not any joke in any respect.
New Borat Malware Doesn’t Imply Any Joke



At the moment, It’s unclear if the Borat RAT is bought or freely shared amongst cybercriminals. Nonetheless, Cycle says it comes within the type of a bundle that features a builder, the malware’s modules, and a server certificates.
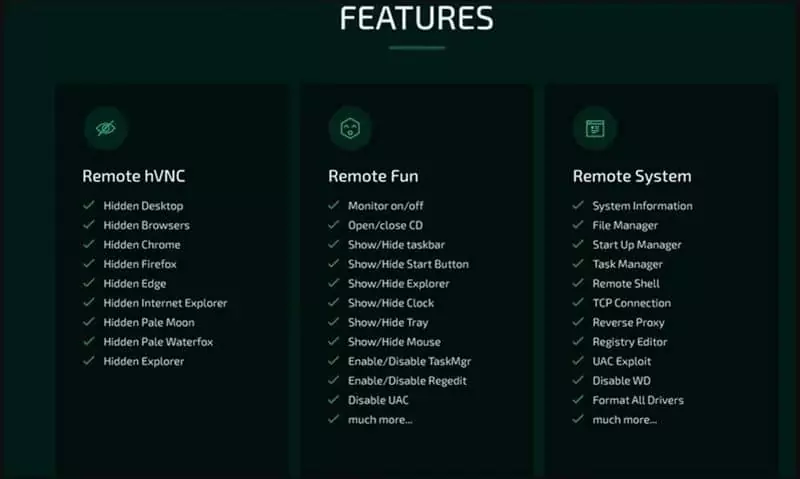
Some outstanding options of the trojan, based on Cyble, embody the next:
- Ransomware – deploy ransomware payloads onto the sufferer’s machine and routinely generate a ransom be aware by way of Borat.
- DDoS – direct rubbish visitors to a goal server by utilizing the compromised machine’s sources.
- Distant desktop – begin a hidden distant desktop to carry out file operations, use enter units, execute code, launch apps, and many others.
- Reverse proxy – arrange a reverse proxy to guard the distant operator from having their id uncovered.
- System information – collect primary system info.
- Course of hollowing – inject malware code into professional processes to evade detection.
- Credential stealing – steal account credentials saved in Chromium-based internet browsers.
Another minor comprises hiding the desktop, hiding the taskbar, holding the mouse, turning off the monitor, exhibiting a clean display, or hanging the system.
Based on Bleeping Computer systems, the above options make Borat a RAT, spyware and adware, and ransomware, so it’s a strong menace that would conduct dangerous actions on a tool.
Particularly, the menace actor is distributing these instruments as cracks for video games and purposes, so watch out to not obtain something from untrustworthy sources reminiscent of torrents or misleading websites.
Disclaimer: Cyberfreaks doesn’t assist any malware or any cyber exercise. Cyberfreaks is especially in opposition to most of these actions; all above content material is just for info or as preventive.




