When you have been utilizing the Home windows working system for some time, you may be very acquainted with the CMD or Command Immediate. Command Immediate is a command-line interpreter which is usually thought of probably the most highly effective instrument in Home windows. You possibly can run CMD with administrative privileges to entry the core options of Home windows.
Command Immediate is helpful, however hackers typically use it for the improper function. Safety specialists additionally use the command immediate to seek out potential safety loopholes. So, if you’re keen to grow to be a hacker or safety knowledgeable, this put up may enable you to.
Additionally Learn: How To Remove Computer Viruses Using CMD
Listing of 10 Finest CMD Instructions Used In Hacking
On this article, we’ll share among the finest CMD instructions broadly used for Hacking functions. So, let’s take a look at the checklist of finest CMD instructions for Home windows 10 computer systems.
1. ping
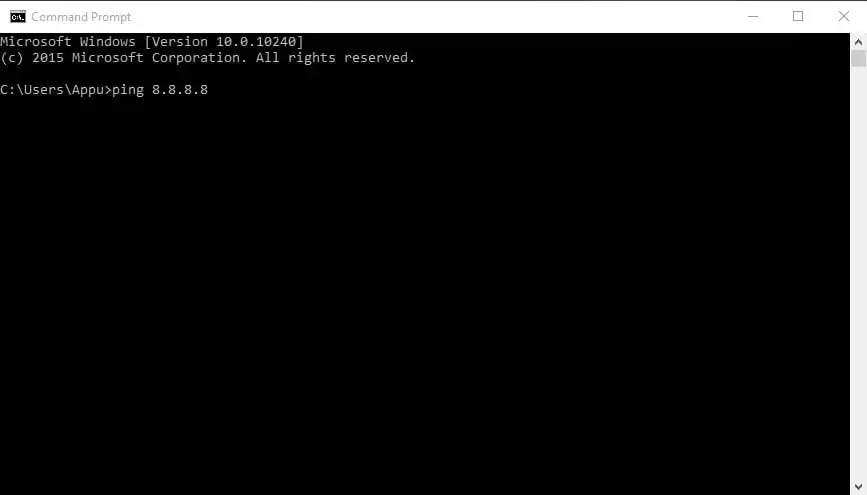
This command makes use of your web connection to ship some packets of knowledge to a particular internet handle then these packets are despatched again to your PC. The check exhibits the time it took to achieve the precise handle. Merely put, it helps you realize if the host you’re pinging is alive.
You should utilize the Ping command to confirm that the host pc can hook up with the TCP/IP community and its sources.
For instance, you’ll be able to kind within the command immediate ping 8.8.8.8, which belongs to Google.
You possibly can exchange “8.8.8.8” with “www.google.com” or one thing else you need to ping.
2. nslookup
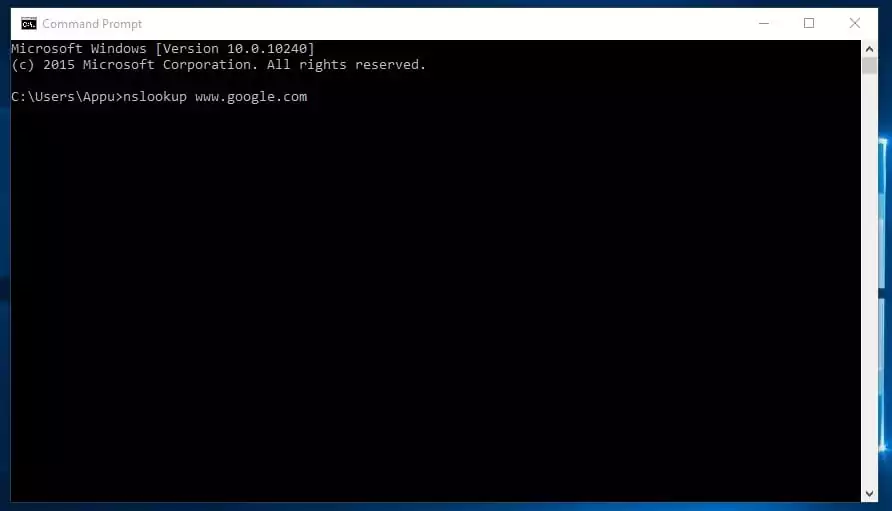
It’s a community administration command-line instrument that helps you get hold of area identify or IP handle mapping for any particular DNS file. The nslookup is usually used for acquiring the server data.
Suppose you’ve an internet site URL however need to know its IP Handle. You possibly can kind in CMD nslookup www.google.com (Change Google.com together with your web site URL of which you need to discover the IP handle)
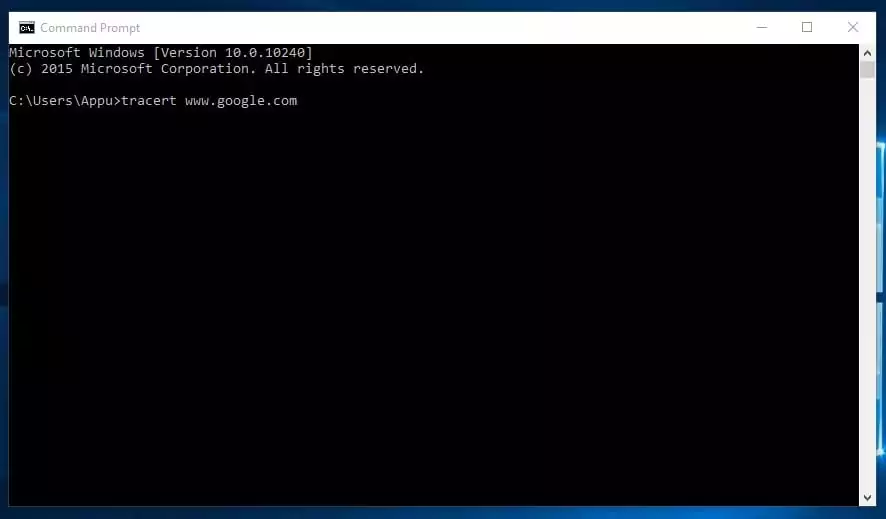
3. tracert
You possibly can say Hint Route. Like its identify, it permits customers to hint an IP’s route to achieve a vacation spot. The command calculates and shows the time every hop took to achieve a vacation spot. It is advisable kind
tracert x.x.x.x (if you realize the IP Handle) or else you’ll be able to kind tracert www.google.com (In the event you don’t know the IP handle)
4. arp
This command lets you modify the ARP cache. You possibly can run an arp-a command on every pc to see whether or not the computer systems have the proper MAC handle listed to ping one another to succeed on the identical subnet.
This command additionally helps customers discover out if anybody has finished arp poisoning of their LAN.
You possibly can strive typing arp-a within the command immediate.
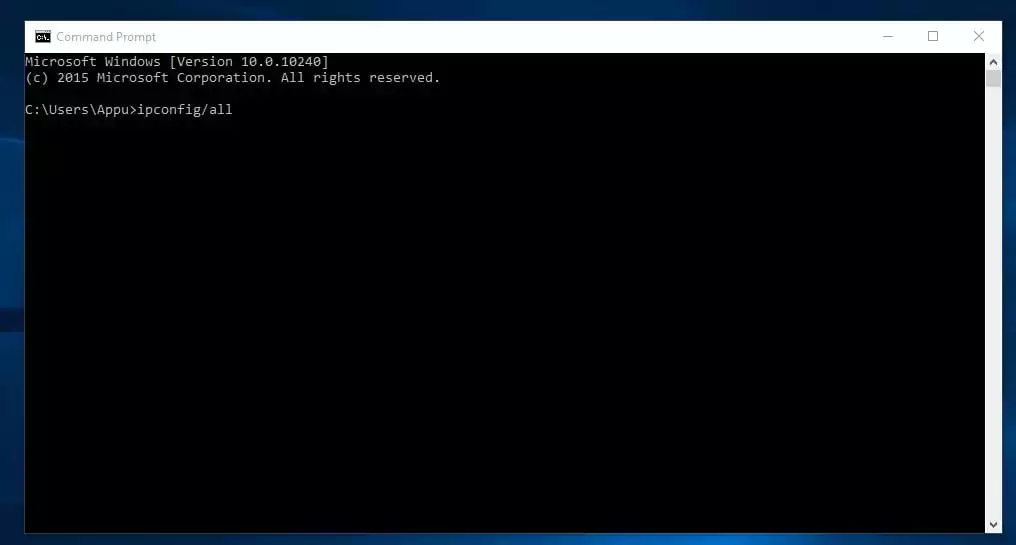
5. ipconfig
That is the command which exhibits each helpful factor. It’s going to present you the IPv6 handle, short-term IPv6 handle, IPv4 handle, Subnet Masks, Default gateway, and all different stuff you need to find out about your community settings.
You possibly can kind within the command immediate “ipconfig” or "ipconfig/all"
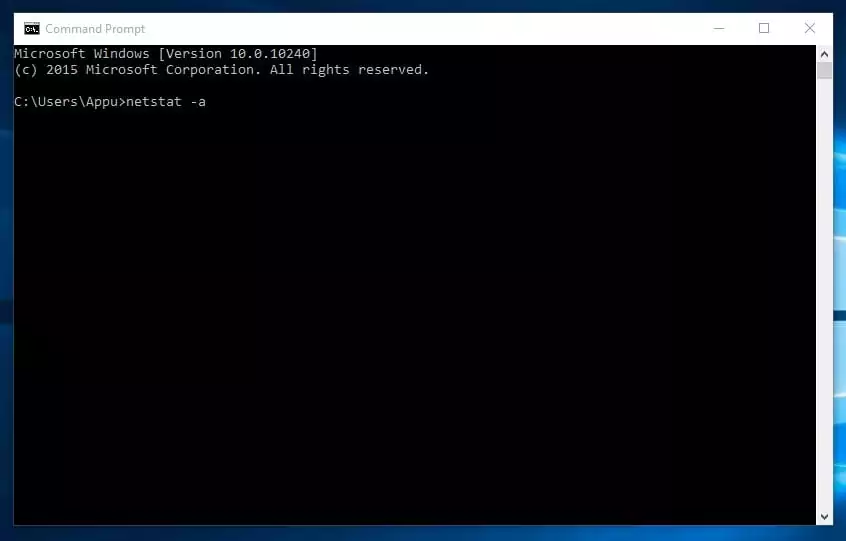
6. netstat
If you wish to discover out who’s establishing a connection together with your pc, you may strive typing within the command immediate “netstat -a”. It’s going to show all of the connections and get to know in regards to the energetic connections and listening ports.
Kind in command immediate "netstat -a"
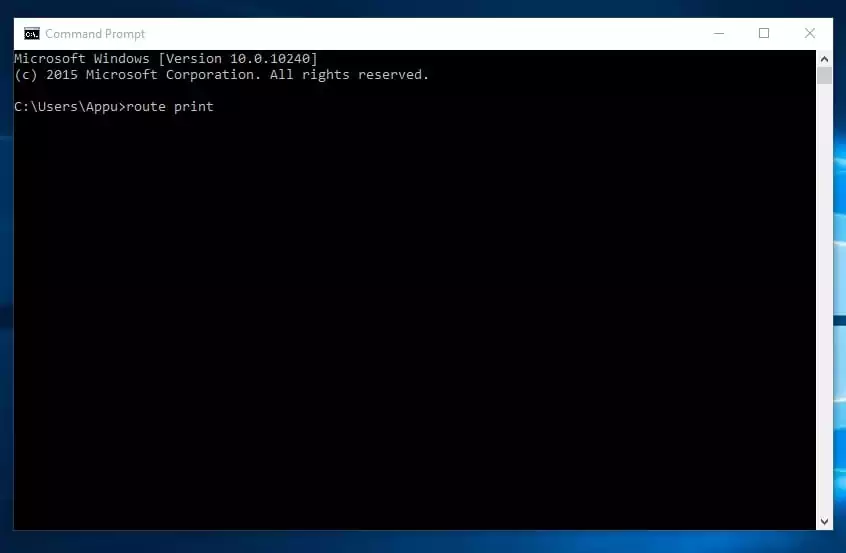
7. Route
It’s a command used to view and manipulate the IP routing desk within the Microsoft Home windows working system. This command will present you the routing desk, metric, and interface.
Hackers typically use the Route command to tell apart between routes to hosts and routes to community. You possibly can kind within the command immediate "route print"
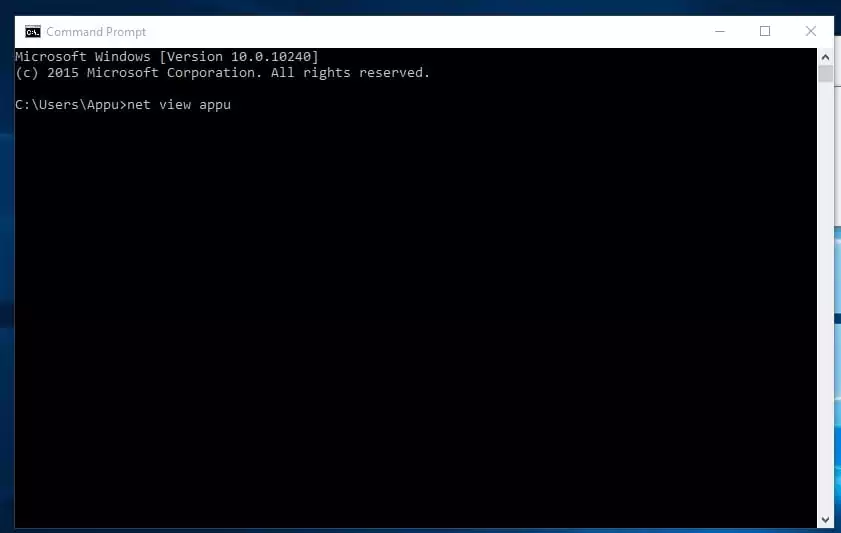
8. Web View
This command shows the checklist of sources, computer systems, or domains shared by the desired pc.
On Home windows, you should use the Web View command to seek out computer systems in your community whose community discovery is turned on.
You possibly can kind within the command immediate "web view x.x.x.x or computername"
9. Tasklist
This command opens up a whole job supervisor on the command immediate. Customers must enter the tasklist on CMD, and they’re going to see the checklist of all working processes. You possibly can work out all of the wrongs with these instructions.
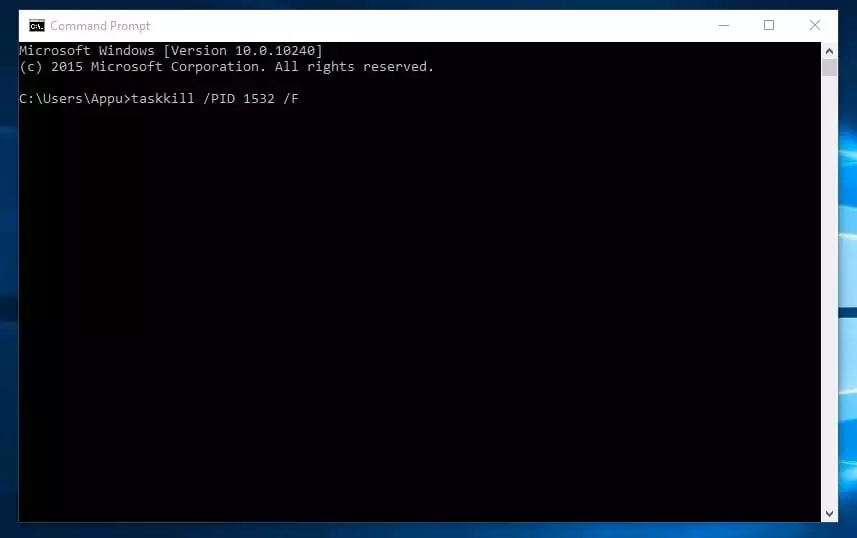
Furthermore, you can too use the command to shut any course of forcefully. For instance, if you wish to kill PID 1532 course of, then you’ll be able to enter the command:
taskkill /PID 1532 /F
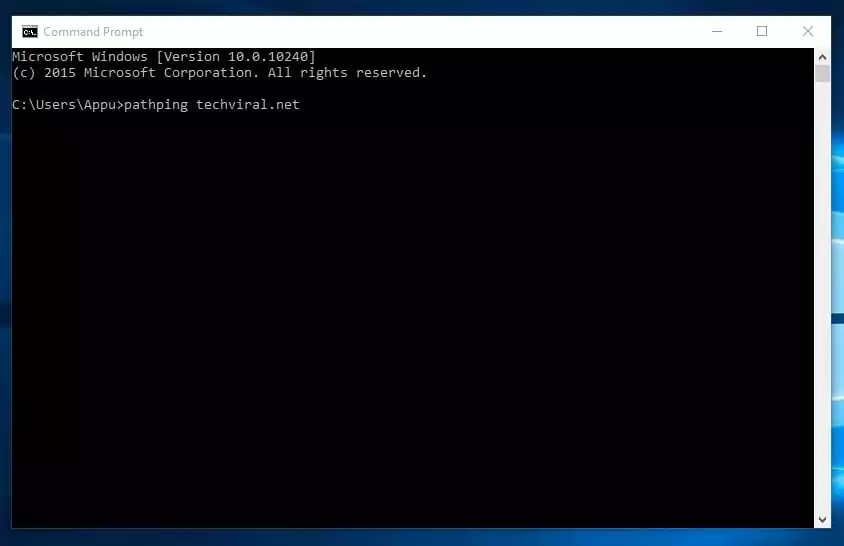
10. Pathping
Nicely, pathping command is just like the tracert, but it surely exhibits extra detailed info.
The instructions take just a few moments to finish because it analyzes the route taken and computes packet loss. On the Home windows command immediate, kind within the following command
pathping Cyberfreaks.web (Change Cyberfreaks.web with the one that you simply need to ping)
So, above are the perfect CMD instructions utilized in hacking. You possibly can discover greater than this; we now have listed the Best CMD commands in one in every of our articles! I hope you just like the put up! Please share it with your folks too. Depart a remark beneath if you wish to add any command to the checklist.